What Is Rasp Security And The Reasons Why It Is Important?
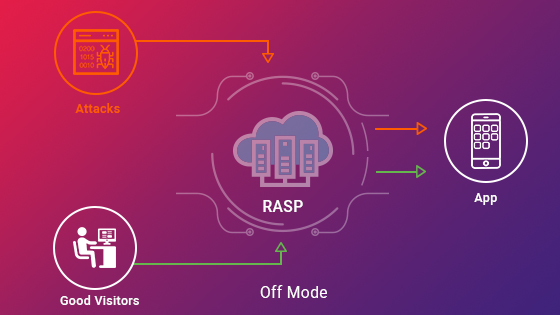
RASP turns out to be an emerging form of security technology that prevents an organization to stop the attempts of hackers for compromising enterprise applications and data. Developed into an application or an application runtime environment, RASP is capable of controlling the execution of application. On to the running application it is known to incorporate security when it resides on the server. Since it is server based it can detect, block and mitigate attacks where it is known to protect applications on a real time basis. RASP does have an ability to protect an application from data theft, behaviour and malicious inputs and all of them without human intervention.
The Reasons Why Rasp Security Is Important?
Technologies in the form of WAP and IPS are used for application protection at runtime, but they are known to work in line as they inspect network traffic and content. Since it is known to analyse traffic or user sessions, it is not possible for them to witness on how traffic or data is processed with applications. Their proactive measures do lack the accuracy required for termination of the session as they consume considerable degree of security bandwidth used for alerts or log collection. The need of the hour is a new type of protection application referred to as RASP security that resides with in to be protected by the run time environment of an application.
Their Working
RASP turns out to be a popular form of technology that intercepts the calls from an app on to the system. It validates data request directly on to the app. Hence it is known to enhance the overall application security where it monitors inputs and blocks those that would lead to attacks. Hence it protects the runtime environment from unwanted changes or tampering. RASP vendors do provide unprecendted protection along with visibility which blocks attacks in a quick and effective manner till you are able to address the underlying vulnerabilities. The two primary capabilities of RASP are
- Application threat intelligence- provide inputs to the security team on how is attacking, the methods that they are using as the applications they are targeting on to the code level
- Application protection- Stopping of application vulnerabilities in an accurate manner from exploitation without disrupting the genuine application use.
The Benefits
The RASP is unique as it is known to work from the interiors of the software and it is not a network device. This will allow RASP to take advantage of the entire conceptual information that is available inside the API or runtime application, including the network configuration, code, application server configuration. More the context points to broader protection and better levels of accuracy.
Rasp Provides Lower Opex And Capex
- The solution of RASP is known to block attacks quickly till the point the underlying capabilities are addressed.
- It is less expensive to deploy and operate than a WAF
- They deploy on to the existing servers and avoids capital expense
- RASP technology ends up observing what an application goes on to perform, will not require the same form of tuning, verification, model building along with human resources
Rasp Accuracy Means More Protection Of Applications
If you are protecting applications means that you need to block them at a network level. Though legacy approaches tend to be inherently accurate when the question of understanding application behaviour evolves since it is outside the application itself. Even the network based security products generate generates a lot of false positives and requires tuning. In the last few years, network protection has made a move over to the application from the WAP to the firewall. With RASP security has moved closer to the application

- RASP instrumentation provides a level of accuracy that is not possible with legacy approaches
- Application protection is to be positioned literally as part of the application
- An increase in accuracy transforms the adoption equation, where organizations are able to protect their data properly
Rasp Tends To Be Devops And Cloud Ready
- RASP is known to work well with agile development, web services and cloud apps
- It is known to accelerate agile development by providing protection without rework unlike WAF solutions that may require constant tuning
- RASP solutions is known to provide actual application behaviour, as there is no longer any need to develop statistical models.
- RASP is known to move in a seamless manner with the application, be in on premises or the cloud as the application is known to scale up and down.
- RASP tends to be faster and a lot accurate
Rasp Turns Out To Be An Excellent Choice When The Question Of Application Layer Attacks Emerge
- RASP is going to provide you with regular information about who is attacking you. The techniques that you are using or the data assets that is under target.
- Apart from the HTTP requests. RASP is bound to provide details about the application about the techniques they are going to use.
- It is going to provide visibility on to software development teams, that helps to prioritize work and take necessary action in case of security defence.
As RASP does not turn out to be a hardware box, in all the environments it may be employed including testing and deployment. RASP will provide constant visibility on to the application attacks and quickly stop the hacks. The net result is that application may be able to defend attacks and that too in real time.
A platform like appselling would turn out to be the perfect solution in such cases. Application security has seldom become a topic of change among developers where testing and security of the application is important. RASP is known to use deep security instrumentation to gain an idea on how attacks behave and protection directly on to the applications without not requiring any changes. There is no need to be learning about applications as it is known to become part of it in a major way. No changes in the runtime environment is also necessary.







